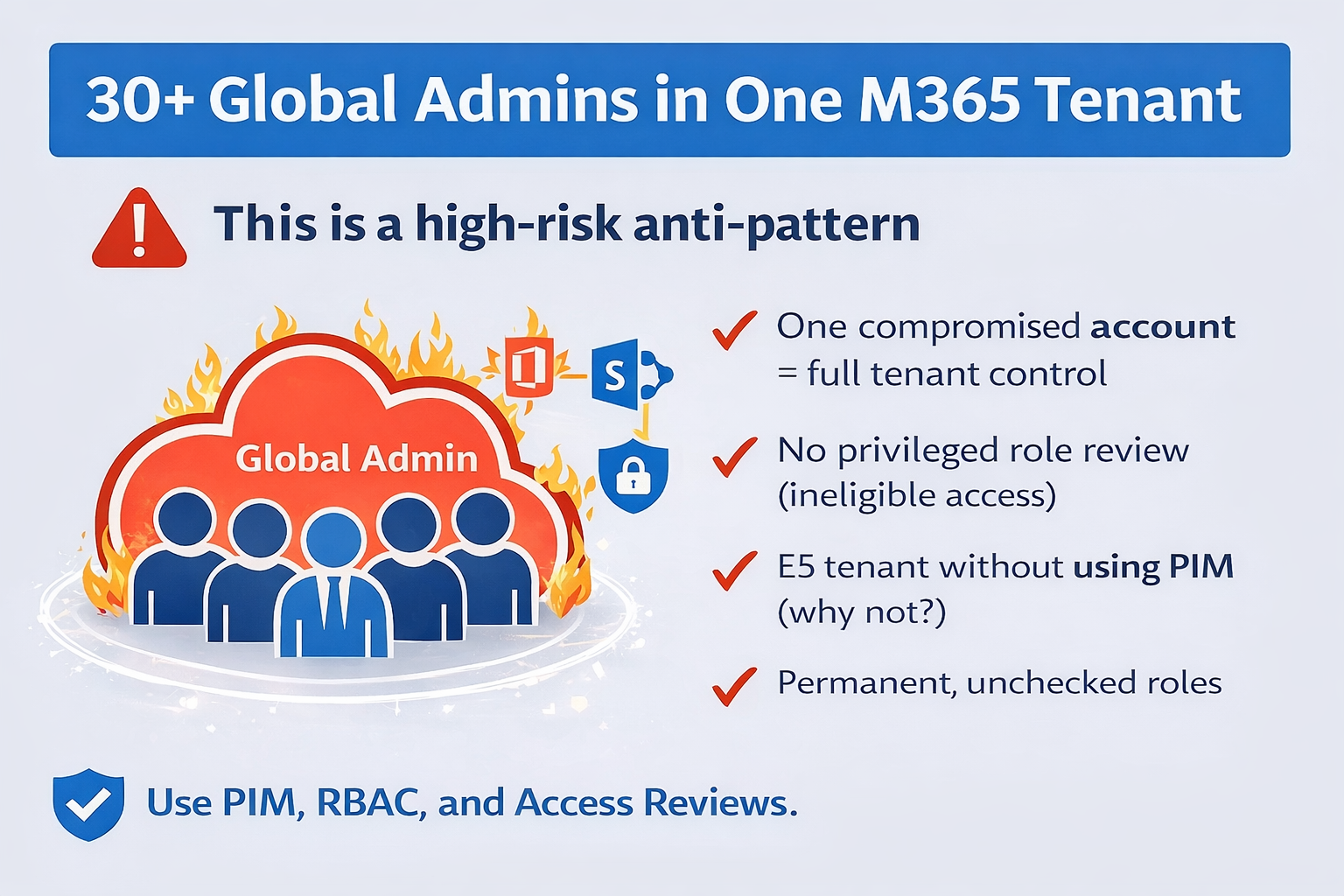
I recently came across a Microsoft 365 tenant with 30+ Global Administrators. What made this more concerning wasn’t just the number, it was that:
- The tenant had E5 licensing.
- Privileged Identity Management (PIM) was available.
- No eligible role assignments were being used.
This isn’t a rare scenario. I left what I was talking about in middle to explain to them why this is a serious identity and security risk.
Why Global Admin sprawl is dangerous
A Global Administrator role has more power than many organizations realize.
A Global Admin can:
- Disable or bypass Conditional Access
- Grant themselves or others any role
- Access or exfiltrate sensitive data
- Modify identity and security configurations
- Delete audit logs
- Effectively take full control of the tenant
If one Global Admin account is compromised, the blast radius is the entire organization.
Treating Global Admin as a convenience role dramatically increases risk, especially in large or distributed teams.
How many Global Admins should a tenant really have?
In most environments:
- 5 – 6 Global Admins is more than sufficient
- These should typically be limited to:
- Break-glass accounts
- A small core identity/security team
- Everyone else should be eligible, not permanently assigned.
When I see tenants with dozens of Global Admins, it usually points to:
- Poor role design
- Legacy access that was never cleaned up
- “Just give GA, it’s faster” culture
Convenience today becomes risk tomorrow.
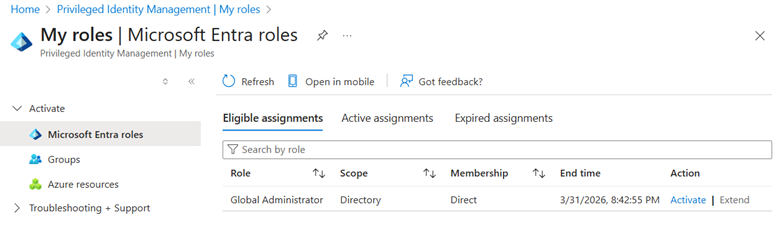
If you have E5, there’s no excuse not to use PIM
With Privileged Identity Management, organizations can:
- Make Global Admin eligible instead of permanent
- Require MFA and justification for activation
- Limit activation duration
- Log and audit every elevation
Permanent Global Admin access should be the exception, not the default. Using PIM turns privilege into a deliberate, time-bound decision, instead of a standing entitlement.
Learn more – Start using PIM – Microsoft Entra ID Governance | Microsoft Learn
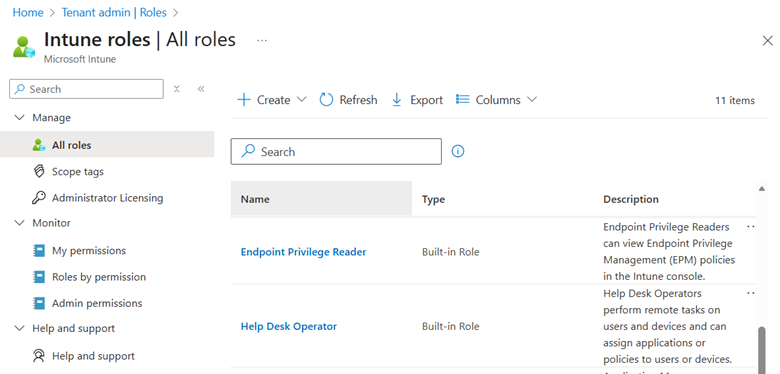
RBAC exists for a reason, use it
Most users assigned Global Admin don’t actually need it.
Instead:
- Use least-privileged Entra ID roles
- Use Intune RBAC for endpoint and device teams
- Use Exchange, SharePoint, Security, or Compliance Admin roles where appropriate
- Separate identity, security, and endpoint responsibilities
Good RBAC design reduces risk without slowing teams down. If everyone needs Global Admin to do their job, the problem isn’t Microsoft, it’s role design.
RBAC in Entra ID – Overview of Microsoft Entra role-based access control (RBAC) – Microsoft Entra ID | Microsoft Learn
RBAC in Intune – Role-based access control (RBAC) with Microsoft Intune – Microsoft Intune | Microsoft Learn
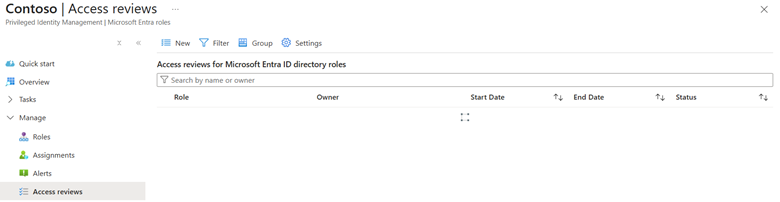
Access Reviews: the control most tenants ignore
Even when roles are assigned correctly, access becomes stale over time.
People:
- Change roles
- Move between teams
- Join temporary projects
- Leave the organization
This is exactly why Access Reviews in Entra ID exist. With Access Reviews, organizations can:
- Periodically review privileged role assignments
- Automatically remove access if it’s not re-approved
- Delegate reviews to managers or role owners
- Enforce governance without manual audits or spreadsheets
Yet in many tenants, this capability is licensed but unused.
Learn more – What are access reviews? – Microsoft Entra – Microsoft Entra ID Governance | Microsoft Learn
PIM without Access Reviews is incomplete
Using PIM is a strong first step, but without Access Reviews:
- Eligible roles quietly accumulate
- Privileged access becomes long-lived again
- Risk slowly creeps back in
A mature identity governance model combines:
- RBAC to limit scope
- PIM to control elevation
- Access Reviews to continuously validate access
Together, they ensure privilege is earned, time-bound, and regularly re-evaluated.
Identity must reflect reality, not org charts.
If access doesn’t change when:
- Someone changes roles
- A contractor’s engagement ends
- A project wraps up
Then identity governance is already out of sync with reality. Security tools don’t fail organizations, unchecked privilege does.
All I want to say is Global Administrator is not a convenience role. It’s a business-critical risk decision. Organizations don’t need more Global Admins, they need better role design, controlled elevation, and continuous review.